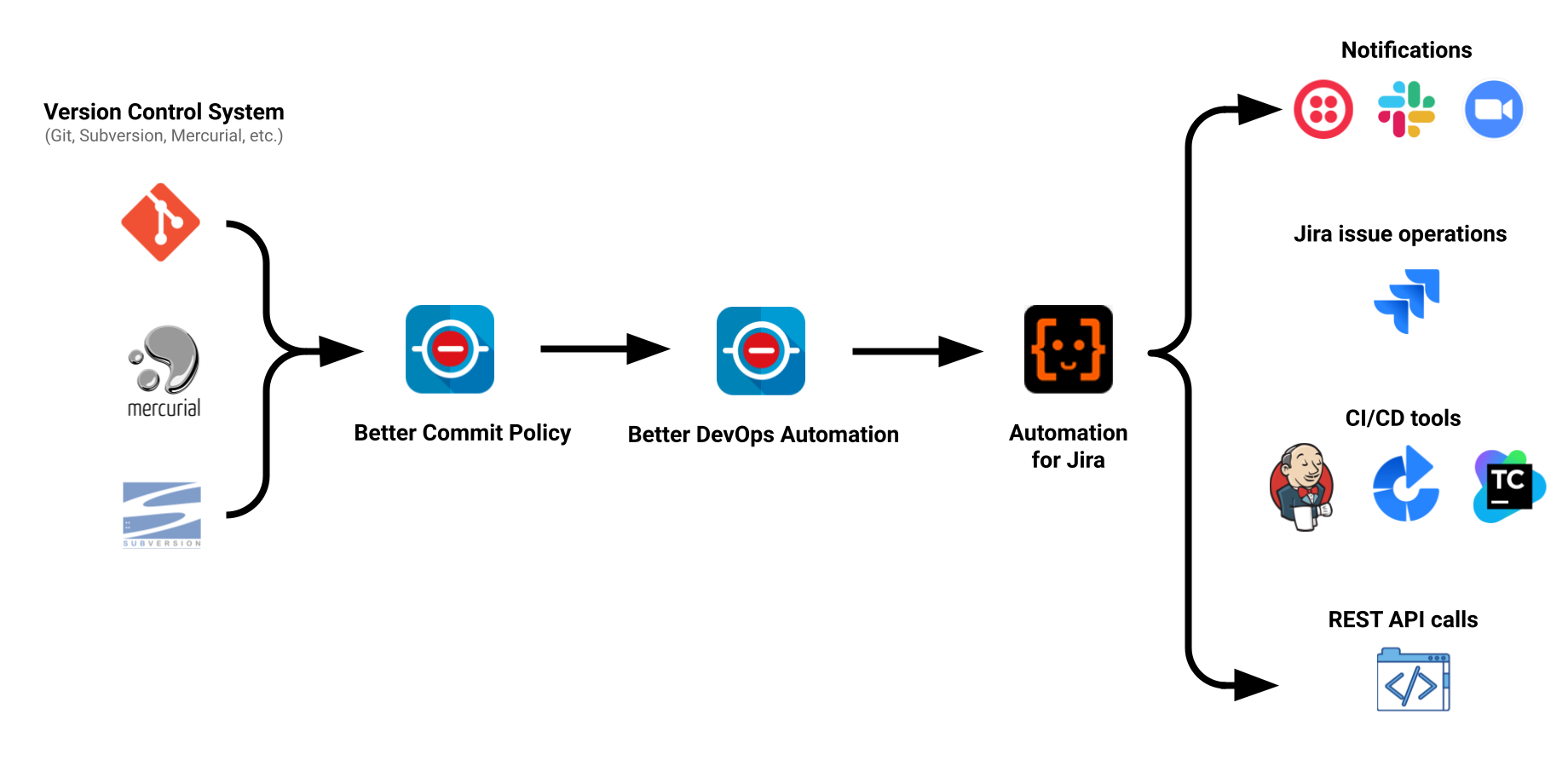
Better Commit Policy for Jira Server
Automatically check Git, Bitbucket, GitHub, GitLab, Subversion & Mercurial commits and pull requests against configurable rulesHow does it work?
Better Commit Policy checks your commits and pull requests against configurable rules. Commits and pull requests that break the rules are blocked until fixed.
Enforce development standards
- validate links between commits, pull requests and Jira issues 🔗
- maintain a well-structured commit history
- ensure traceable changes
- speed up code reviews ⚡
- stay audit-ready
- promote standards-based development
← Learn more by watching the intro video in the left.
Stay in control of every code change
Rules can be limited to:
- specific branches 🌱
- specific directories 📁
Rules can check every commit detail:
Supports the Version Control System you already use
Built for everything from centralized VCS to cloud-native distributed VCS.
- Git
- Git (client-side) (must-have for Git users!)
- Bitbucket Server (via a free Bitbucket app)
- Bitbucket Data Center (via a free Bitbucket app)
- Bitbucket Cloud
- GitHub
- GitHub Enterprise
- GitLab.com
- GitLab Self-Managed
- Subversion
- Mercurial
- Perforce
- TFS (Team Foundation Server)
- ClearCase
... plus any other VCS or environment via the REST API and custom hook scripts!
Ready for the Enterprise
Unlike free or home-grown solutions, Better Commit Policy is:
- Commercially supported
- Scalable (for enterprise-scale teams using Jira and Bitbucket)
- Secure (SOC 2 Type II, vulnerability scanner, bug bounty program)
- Maintained for new Jira releases (both Cloud and Data Center)
- Well-documented
Catch bad commits before they happen
Fixing bad commits later? Total pain.
Better Commit Policy checks your commits before they're created. ⚡Other commit checker apps for Jira wait until you push. Too slow. Too late.
Works with your current tools
Your team can keep using any standard-compliant VCS client (command-line, GUI tools, IDE integrations) on any OS.
Zero learning curve
After a couple of rejections, clean commits become second nature. ✨
Atlassian Open DevOps experience on Jira Server 
Make Jira your DevOps backbone with the help of Better DevOps Automation, a companion app for Better Commit Policy.
Automate development workflows
Free up developers from repetitive and error-prone manual tasks.
Use Commit Created, Branch Created, Tag Created triggers or @commands (entered in commits messages) to automatically notify on, build, deploy, deliver or scan your code!
Enforce well-formatted and traceable commit messages
Ensure every commit is traceable, properly formatted, and linked to the right Jira issue.
-
Commit message must match a pattern
- commit messages must start with a Jira issue key
- commit messages must be 10+ characters long
-
Commit message must contain issue keys from a JQL query
- commits must be linked to one or more valid Jira issues
- commits must be associated with exactly one story in the current sprint
Validate the branches your developers create
Enforce your branches are standardized and follow your naming conventions.
-
Branch name must match a pattern
- branch names must follow naming conventions (example: must start with feature/, bugfix/ or hotfix/)
- bugfix type branch names must contain a test execution ID (example: "bugfix/1741-test-run")
-
Branch name must contain issue keys from a JQL query
- story type branch names must include a "Story" type issue from the currently running Scrum sprint (example: "story/CAL-123-shared-calendars")
- bugfix type branch names must include a "Bug" type issue assigned to the commit author (example: "bugfix/CAL-345-form-validation-crash")
Protect your repository from unexpected files and changes
Keep your repo clean, and your codebase protected.
-
Changed paths (files) must match a pattern
- protected paths: lock the "/doc/legal" directory from modifications
- accept only image files in the "/static/images" directory
- reject *.tmp, *.cfg, *.obj, *.class, .* and other temporary or hidden files
-
Changed paths (files) must contain issue keys from a JQL query
- filenames in the "/patches" directory must include a "Bug" type issue (example: "/patches/CAL-123.patch")
- sub-directories in the "/test/data" directory must be linked to a "Test" type issue (example: "/test/data/CAL-456/japanese.json")
Rigorous change control
Establish processes for compliance with ISO standards, IEC standards and industry regulations in:
- defence
- financial
- avionics (success story)
- automotive
- medical
- pharmaceutical
- other safety-critical systems
Or, just make sure that every change to your code is introduced in a controlled and documented way!
End-to-end traceability
Accelerate requirements validation, compliance verification, impact analysis, coverage analysis and source code audits by bi-directionally linking Jira issues and source code changes:
- requirements ⇔ code changes
- epics ⇔ user stories ⇔ code changes
- tasks / bugfixes ⇔ code changes
- tests ⇔ code changes
- change requests ⇔ sub-tasks ⇔ code changes
- releases ⇔ issues ⇔ code changes
Faster code reviews & audits
Maintain development workflows for consistent repository, code & history.
By making small improvements (useful tips) in the way your team works, common questions like these will be automatically answered:
- "Why was this changed?"
- "Was it tested? In what environments?"
- "Is this within the scope of the current release?"
- "Who approved this merge?"
- "Is there a programmatic test for this story?"
Why should I care about change control?
- Computer system failure cost British Airways $100 million
- Gartner estimates network downtime may cost $300K per hour (average)
- Software failures cause 24% percent of all the medical device recalls according to FDA
- Forrester estimates that Amazon Web Services (AWS) outage affected 100,000 sites
- Software bug would allow hackers to take control over Sydney nuclear plant
- Unauthorized changes disable $2.7 billion US Navy submarine
Integrated with the VCS tools you already use
How does it help me work better?

Helping the developer team comply with regulations and software requirements
"In the aviation industry, we need to be able to prove to authorities how exactly each aerospace system requirement is fulfilled and by what part of the source code.
Better Commit Policy makes it easy to manage our Jira work items towards those requirements, proactively control what is committed to our source code repositories, and ultimately, to comply with regulations."
– Kalen Brown, Associate Electrical and Computer Engineer
Read the story →
How developers of safety-critical systems at Philips manage source code changes
"Before using commit policies, our developers’ behavior was like in the wild west.
We couldn’t match source code changes with Jira issues, it was almost impossible to understand what work has really been done, we wasted time.
The Better Commit Policy app helps us maintain a manageable development process by enforcing some configurable rules in a friendly, but strict way."
– Yakov Yukhnovetsky, DevOps Engineer
Read the story →Who's using it?














I really believe, every software company must incorporate it into its developing process.
This is a must have to have a clean repository. The ability to check the rules also locally is just great.
What I liked here, the plugin didn't force me to change how my developers want to interact with the repositories: in command line, in Bitbucket, in Jira, in any type of git clients.
Not only does this plugin provide exactly the features we were looking for, it was easy to setup with clear instructions. Support was great - extremely helpful, responsive and polite.
more reviews →While the plugin is great, the support is even greater (shout out to Gabor)! The initial environment setup was fairly easy. Just set it and forget it.
Evaluation: try before you buy
- Install the app. (how to install?)
- Get your free trial license that allows using the app without limitations for 30 days. (how to try?)
- When the trial is over, continue using the app by purchasing a commercially supported license. (how to buy?)
- Ask questions or report problems any time by clicking the "Help" tab in the right bottom. (how to get support?)
- Get the latest Better Commit Policy for Jira release announcements, best practices, tips from power users. (how to subscribe?)